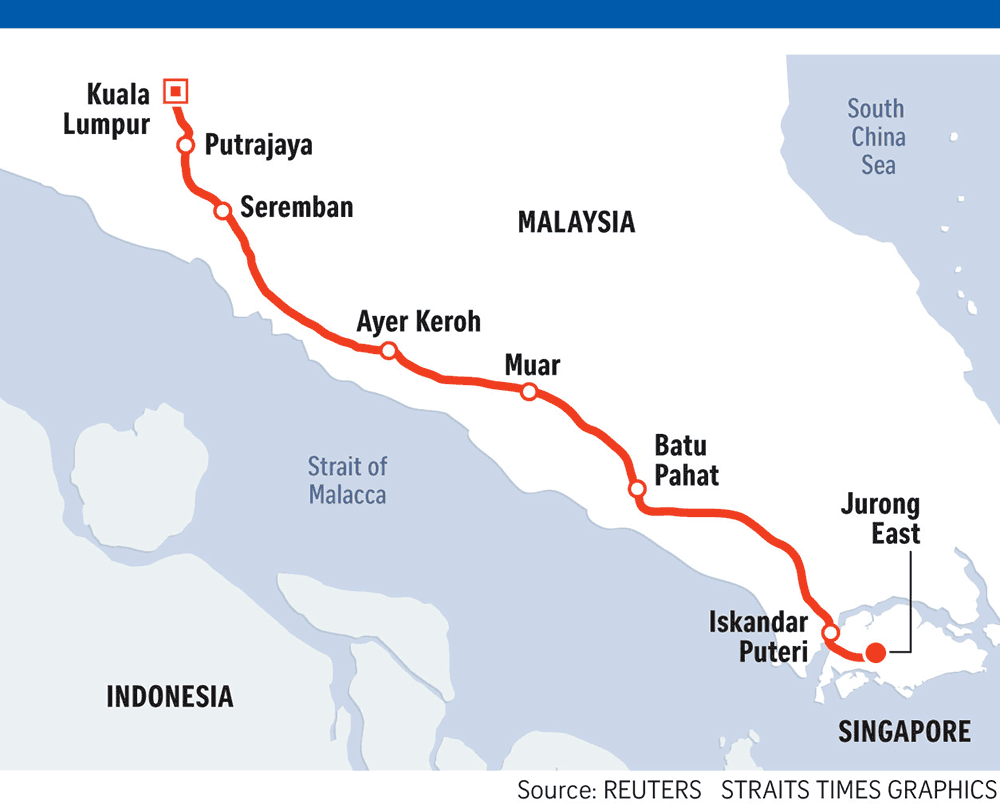
The Japanese company that has expressed the bid for the construction of the Malaysian high speed railway is Shinkansen. A company with a long and impressive history with high speed railway development.
Not only does Shinkansen hold the record for the fastest high speed railway in the world, it also boasts impeccable safety accomplishments. The Japanese high speed railway has not had a single fatal accident in more than 50 years, despite having passenger numbers that have surpassed 10 billion.
The Japanese regularly smashes its own speed records, establishing and breaking its own top-speeds in 1997, 1999, 2003, 2015 and recently when the Japanese Maglev reached speeds of 603 km/h in 2016.
The train that broke the recent 2016 record, the floating Maglev, earned its name because, unlike traditional trains, the Maglev doesn’t use metal train tracks. Instead, it floats 10cm above the rails through the use of magnetism. The magnetic levitation means that the train has no contact with the ground whatsoever, allowing for friction-less movement.
Shinkansen’s advanced technology has not only been used inside Japan, but has also been adopted by other countries like China’s CRH2 Railway, which is designed after Shinkansen’s E2-1000 series. Or Taiwan’s high speed rail which operates the 700T series which was built by Japanese engineers. India also decided to adopt the Japanese high speed railway system. In addition, the Japanese system, Shinkansen, is expanding to Thailand and the US.
If the Japanese Maglev technology was applied to the Malaysian high speed railway, it would take about 50 minutes to reach Singapore from Kuala Lumpur.